LDAP CheatSheet. GitHub Gist: instantly share code, notes, and snippets. Set objRootDSE = GetObject('LDAP://rootDSE') Set objContainer = GetObject('LDAP://cn=Users,' & objRootDSE.Get('defaultNamingContext')) For i = 1 To 1000 Set objLeaf = objContainer.Create('User', 'cn=UserNo' & i) objLeaf.Put 'sAMAccountName', 'UserNo'. Running ldapsearch using simple authentication $ ldapsearch -x -b 'dc=fulltilt,dc=com' 'userName=.' Running ldapsearch using simple authentication and the rootdn. (Passwords won’t show up in the result unless bind is done this way.).
| Symmetric [Performance] | CipherType | Asymmetric (Public Key) [Key Exchange] |
|---|---|---|
| Vernam (One Time Pad) Used in WWII in the German Enigma | XOR | RSA (Rivest, Shamir & Aldeman) - Uses large prime numbers. Encrypt/decrypt digital signatures. |
| AES (Advanced Encryption Standard) [Rijndael] (128, 192, 256 bits) Used by WPA2. (Data at rest) | Block | DSA (Digital Signature Algorithm) - Modifies Diffie-Hellman for use in digital signatures. Combines with elliptic curves to create ECDSA. |
| DES (Data Encryption Standard) [Lucifer] (56 bits) Easily brute forced. | Block | Diffie-Hellman Key Exchange (DH) - A standard for exchanging keys. Primarily used to send private keys over public networks. ECDHE (Elliptic Curve DH) Used for perfect forward secrecy. |
| 3DES (2 keys - 112 bits & 3 keys - 168 bits) Not used today. | Block | ECC (Elliptic Curve Cryptography) - Needs large integers composed of two or more large prime factors. Great for low powered machines bc uses less CPU. Uses curves instead of prime numbers. |
| RC4 (Rivest Cipher 4) (40-2048 bits) Used by WEP and WPA.[deprecated] | Stream | PGP (Pretty Good Privacy) - Used for emails and is used by IDEA algorithm; GPG(GNU Privacy Guard): A free version of PGP with sames specs. |
| Blowfish (1-448 bits) Fast, not patented limited. | Block | |
| Twofish (256 bits) | Block | Hashing Algorithms - Integrity |
| E0. Used by BlueTooth | Stream | MD5 (Message-Digest Algorithm v5) - 128 bit digest. Collision was found so it is not used as much. |
| SHA (Secure Hash Algorithm) - 160 bit digest. Standard today. Wnet from SHA-1(160 bit) to SHA-2(512 bit). by NSA. | ||
| Block cipher modes | HMAC (Hash-Based Message Authentication Code) - Combines itself with a symmetric key. Used in network encryption protocols. | |
| CBC (Cipher Block Chaining) - Symmetric, uses IV. Slow | RIPEMD (RACE Integrity Primitives Evaluation Message Digest) - Based on MD4. Collisions were found. | |
| GCM (Galois Counter Mode) - Encryption with auth. Very efficient. Provides data authenticity/intregrity. Widely used. | ||
| ECB (Electronic Code Book) - Simplest mode, each block with same key. Not recommended. | SSL (Secure Sockets Layer) protocol - Has two parts. The SSL Handshake Protocol establishes the secure channel. And the SSL Application Data Protocol is used to exchange data over the channel. 6 Steps in the handshaking process. | |
| CTR (Counter Mode) - Converts block into stream, uses IV. Widely used. | ISAKMP (Internet Security Association and Key Management Protocol) - Used to negotiate and provide authenticated keying material for security associations in a protected manner | |
| X.509 - A standard defining the format of public key certificates. Used in many Internet protocols, (TLS/SSL) and offline applications, like electronic signatures. Contains a public key and an identity, and is either signed by a CA or self-signed. | ||
| Wireless [Crypto protocols] | Perfect Forward Secrecy (PFS) - Prevents point of failure where a stolen private key can decrypt all connections by generating a new key each session. Protects past sessions against future compromises of secret keys. | |
| WPA (Wi-Fi Protected Access) - Uses RC4 with TKIP. Replaced by WPA2. | S/MIME, or Secure/Multipurpose Internet Mail Extensions, is a technology that allows you to encrypt your emails. S/MIME is based on asymmetric cryptography to protect your emails from unwanted access. | |
| WPA2 (WPA v2) - Uses CCMP for encryption and AES. | ||
| CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) - Is based on 128-bit AES. | ||
| TKIP (Temporal Key Integrity Protocol) - Mixes a root key with an IV, a new key for each packet. Prevents replay attacks and protects against tampering. | ||
| WEP (Wired Equivalent Privacy) | ||
| Goals of Cryptography | ||
| Wireless [Auth protocols] | Confidentiality - Asymmetric (Public Key) & Symmetric Encryption | |
| EAP (Extensible Authentication Protocol): Authentication framework that provides general guidance for authentication methods. | Authenticity/Authentication/Accountability - Asymmetric Encryption (Private Key), MAC/MIC, & Digital Signature | |
| PEAP (Protected EAP): An extension of EAP that is sometimes used with 802.1x, a certificate is required on the 802.1x server. | Integrity - Hashing, Checksum, Parity and Check Digit | |
| EAP-FAST (EAP Flexible Authentication with Secure Tunneling): A Cisco-designed replacement for Lightweight EAP, supports certificates. | Non-Repudiation - Digital Signature (Only) | |
| EAP-TLS (EAP Transport Layer Security): One of the most secure EAP standards and is widely implemented on many networks. It uses PKI, so certificates are required on the 802.1x server and on the clients. | ||
| EAP-TTLS (EAP Tunneled TLS): Allows for systems to use older authentication methods such as PAP within a TLS tunnel. Certificate is required on the 802.1x server but not on the clients. | Diffusion - Changing one character causes the plaintext to drastically change the outputed cipher. | |
| IEEE 802.1x: An authentication protocol used in VPNs, wired and wireless networks. In VPNs it is used as a RADIUS server, wired use it as a port-based authentication, and wireless use it in Enterprise mode. Can be used with certificate-based authentication. | Obfuscation: Taking something and making it difficult to understand, however it is not impossible to convert it back to the original form. | |
| RADIUS Federation: Members of one organization can authenticate to the network of another network using their normal credentials. Uses 802.1X as authentication method. | Confusion - The cipher doesn’t look anything like the plain text. | |
| Public key infrastructure | ||
| Stapling: Combining related items in order to reduce communication steps. The device that holds the certificate will also be the one to provide status of any revocation. | CA (Certificate Authority): A trusted third-party agency that is responsible for issuing digital certificates. | |
| Pinning: The application has hard-coded the server’s certificate into the application itself. | Intermediate CA (Intermediate Certificate Authority): An entity that processes the CSR and verifies the authenticity of the user on behalf of a CA. | |
| CRL (Certificate Revocation List): A list of certificates that are no longer valid, expired, or that have been revoked by the issuer. | ||
| Cert formats | CSR (Certificate Signing Request): A user request for a digital certificate. | |
| DER (Distinguished Encoding Rules): Are common and designed for X.509 certificates, they are used to extend binary encoded certificates. Cannot be edited by a plain text editor. Used with Java commonly. Stores single certificates, certificate chains, or private keys. Uses either a .der or .cer extension. | OCSP (Online Certificate Status Protocol): A request and response protocol that obtains the serial number of the certificate that is being validated and reviews revocation lists for the client. | |
| PEM (Privacy Enhanced Mail): It may contain single certificates, certificate chains, or private keys. Comes in a number of different file extensions: .pem, .crt, .cer, and .key. | Certificate: Digitally signed statement that associates a public key to the corresponding private key. | |
| CER (Certificate File): May be encoded as binary DER or as ASCII PEM. | Object identifiers (OID): A serial number that authenticates a certificate. | |
| P12: Is a PFX extension used in windows. | ||
| PKCS #12 (Public Key Cryptography Standards #12): It may contain single certificates, certificate chains, or private keys, although in most cases it is used to store public/private key pairs. Fully encrypt all the data in the file and require a password to open them. Uses the extension .pfx or .p12. | ||
| RFC (Remote Function Call): A formal document describes the specifications for a particular technology, was drafted by the Internet Engineering Task Force. | ||
| P7B: Is stored in Base64 ASCII, containing certificates and chains but not the private key. |
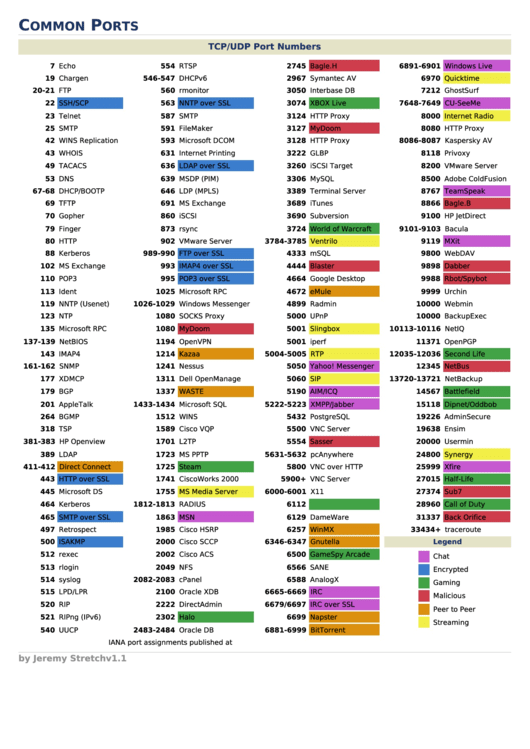
| Port | Use |
|---|---|
| 21 | FTP |
| 22 | SSH/SCP |
| 23 | Telnet |
| 25 | SMTP |
| 53 | DNS |
| 67-68 | DHCP |
| 80 | HTTP |
| 110 | POP3 |
| 143 | IMAP4 |
| 161 | SNMP |
| 389(default)-636(secured) | LDAP |
| 443 | HTTPS/SSL |
| UDP 1701 | L2TP |
| TCP 1723 | PPTP |
| 3389 | RDP |
| 137 | NetBIOS |
| UDP 123 | NTP |
| BIA (Business Impact Analysis) | RTO (Recovery Time Objective) - The start of the interruption and time to establish recovery and end when you can successfully release the service back to your users. |
| MTTR (Mean Time to Recover) - The average time it takes to control and remediate a threat. | RPO (Recovery Point Objective) - Last available restore backup and the maximum time between backups being safely stored offsite. |
| MTBF (Mean Time Before Recover) - The average time between failures. | SLA (Service level agreement) - Defines the level of service expected by a customer from a supplier, laying out the metrics by which that service is measured, and the remedies or penalties, if any. |
| MTTF (Mean Time to Failure) - The length of time you can expect a device to remain in operation before it fails. |
Is it Vintela authentication system or Quest authentication system or Dell or Quest again or One Identity or Safeguard authentication service? I think it depends what version you run and/or when you started using it. Its quite a mess for people who have used the software for last 15+ years but luckily different versions have one thing in common – vastool command-line utility which typically is installed into /opt/quest/bin/vastool. I suggest to verify do you have /opt/quest/bin in your PATH environment variable. This page may be too long to be a cheat-sheet but you can always use search. In some places you might find also comparisons with alternative AD/LDAP integration tool SSSD.
Basic stuff
vastool has a lot of sub-commands, you can see them just by running vastool without any parameters as below. Some vastool sub-commands have also their own sub-sub-commands.
You can always specify user and password in vastool command with -u username and -p password but you can also use a principal host/ if your host is already joined to AD.
NB! USE links below, in the main vastool usage info to jump to relevant command. If there is no link, its not covered…. at least not yet.
If you need help for specific vastool command you can run it with -h command e.g. vastool -h status but it does not work with all commands (like inspect).
vastool status
View status about the operating environment. Really useful to see whats going on like are you joined and so on.
Show basic status information
vastool flush
Flush cached client daemon information. Run it to avoid anomalies after config changes. Can flush by cache or all if you omit command.
Flush all caches:
The latest tweets from @Tygatech. Tyga onlyfans pics reddit. The latest tweets from @tyga.
Hint: vastool flush is same as sss_cache -E if you are using SSSD.
vastool join
Join the computer to the domain. Joining to domain can be done with username /password or username and pre-generated keytab. Username must have join/write privileges in AD so I suggest to generate keytab instead of password and safeguard the keytab as much as possible. Deleting keytab from host right after joining is a good idea and also regular password changes along with the keytab re-generation. It is also possible to implement centralized joining solution so that host-being-joined never sees the credentials, just gets the host keytab.
join host to domain. Command below will join host to domain example.com and creates the computer object in ldap container/path which has DN “OU=Servers,DC=example,DC=com”.
“join” host to domain with pre-generated keytab. useful with centralized joining solution where you actually perform most of the joining actions (create computer object in AD, generate host keytab add SPN-s) on different server. This also means that you don’t need to have high privilege credentials (for AD modifictaions) on target host. Generally this kind of “joining” means only that vastool will generate configuration file vas.conf and configures nsswitch and pam.
Same as previous – define a site and static domain controllers for already joined host. This is useful when you move host to the network where domain controllers cant be located with DNS lookup (SRV record query) and might be also read-only.
AS previous example, this command will also just generate vas.conf and do nsswitch/pam config. This will add following into vas.conf (in addition to the previous config if domain remains the same)
So if you don’t want to run command above, you could just add manually this content to vas.conf and restart the vasd.service assuming nsswitch and pam are already configured.
vastool unjoin
Remove the local computer from the domain. Removes the computer object and disconnects from domain. Also useful to run in the beginning of re-joining if needed.
Unjoin localhost from domain
vastool search
Perform LDAP searches. You can search by any attribute and filter out attributes as you need in the result. Only limitation will be your LDAP query making capability.
Searching user/account attributes, if account is found lists all attributes:
Search account/user group memberships, displays only memberOf attributes:
Note that first line in the search result is account DN, so if you need to calculate number of groups user belongs to, you can send result trough wc and decrease by one or just pipe it trough grep like this
Search account/user by UNIX USER/GROUP ID and list all attributes if found:
Search objects what user is “owning”

Search user mobile / cellphone number
Ldap Filter Cheat Sheet
Search users who’s password never expires and filter out account names.
Search group by group name and list all info – essentially searching groups is done by same sAMAccountName attribute as searching for users.
Search group and display all group members:
Note that first line in the search result is account DN, like the user search few block above.
vastool attrs
List an objects attribute(s). This is a bit similar to vastool search but I guess that you are limited with showing attributes only for one object and cant run any advanced LDAP search queries.
Get GROUP attributes
Get USER attributes
Get COMPUTER attributes (must know DN)
vastool list
List users or groups and their attributes.
List unix-enabled users and groups. Without -l option your query will be run against local cache only and might not reflect very recent changes. As you query local cache you don’t need to use any credentials to run this query.
List all users or groups, including the ones which are not unix-enabled – which do not have user / group ID defined in AD. With -a option you can list also non unix-enabled users but this only seems to work together with -l option. Be careful when using -al – in large environments as its slow and might result in hundreds of thousands lines in result.
List users allowed to log in … or denied. -l option here is not supported. -a option should show you also non-unix-enabled users which somehow e.g. trough group membership should have access to your host (or not with users-denied). I have not tested it but if it works, its a good way to detect login issues like user group access but someone forgot to unix-enable user’s account. Note that users-denied query might have thousands of results in large environments but as it runs against local cache its pretty fast.
vastool user
User account tools. Useful for managing users including checking is user allowed to log in and what configuration e.g. AD group membership grants the access.
Ldap Enumeration Cheat Sheet
Check is user allowed to log in and if it is, what grants it with the sample response
Hint: vastool user checkaccess johndoe is same as sss_ctl user-checks johndoe if you are using SSSD.
vastool ktutil
Manage entries in a keytab. Useful for listing, adding and removing principals in keytab.
list keytab principals. If you don’t specify keytab file with -k option, you get principals list from hosts default keytab.
add host fqdn as alias to short name into keytab. This is very useful to get login with kerberos ticket working. If you have any CNAME-s in the DNS for the host, you need to add them as alias to host keytab and into servicePrincipalName (multi-value) attribute in LDAP.
vastool group
Modify group membership. Adding/removing accounts & computer objects to/from groups.
add localhost to LDAP group
vastool delete
Delete a user, group, computer, service or AD object.
delete computer object with sample output.
vastool create
Create a user, group, computer, or service object in AD.
create computer object in ldap container/path which has DN “OU=Servers,DC=example,DC=com” with sample output.
vastool passwd
Change your password, or set another user’s password
reset computer object password and generate host keytab with sample output. This allows you to join other hosts in centralized way without having to spread credentials. It generates new keytab with random password .
vastool info
View information about the operating environment
generate kerberos config file with vastool info toconf
vastool inspect
Get the value of a configuration setting. Useful to verify contents of the vasd config file /etc/opt/quest/vas/vas.conf and then modify it with vastool configure if needed.
inspect vasd configuration. Below are commands to inspect different configuration parameters in vasd section.
vastool configure
Update configuration files to use the QAS components
configure pam. This configures pam. It is not needed to run it after join as its executed automatically within the join process (but you can skip it during joining). Install mac virtual machine.
configure nss. This adds vas into the list of passwd and group services. It is not needed to run it after join as its executed automatically within the join process (but you can skip it during joining).
configure vas. This allows configuring main vasd configuration parameters online, without manually configuring them in the vas.conf and restarting the service. A good way to learn about the different configuration parameters is man vas.conf
vastool configure vas vas_auth perm-disconnected-users. list of groups or users able to log in even if AD connection is lost, separated by spaces.
vastool configure vas vasd perm-disconnected-update. minutes between updating cached users credentials.
vastool configure vas vasd timesync-interval. hours between timesync. Setting it to -1 makes timesync to run in every 30 seconds and setting it to 0 disables timesync with vasd – useful if you use ntpd or chrony to sync your time.
vastool configure vas vasd user-search-path. Set this to your users OU as best as you can because by default entire AD domain is searched and limiting the scope increases performance especially in the large environments. Configure multiple search paths in same way, just separate them with semicolon.
vastool configure vas vasd group-search-path. Set this to your users OU as best as you can because by default entire AD domain is searched and limiting the scope increases performance especially in the large environments. Configure multiple search paths in same way, just separate them with semicolon.
vastool setattrs
Set object attribute(s)
add servicePrincipalName to computer object. This is quite useful if you have CNAMES defined for your host and you want kerberos to work with them. Note that ServicePrincipalName is multi-value attribute and when you want to update it with some new value, you should specify also the existing ones which are retrievable with attrscommand.
vastool daemon
Manage daemons – this is just a wrapper for service command. You can use it to manage also other daemons, not just the ones related to QAS like vastool. This could be potentially also security issue.
Although the help suggest that you can run only start/stop/status actions against damones like vasd and ipmon, you can run all actions supported by service command against all daemons:
vastool auth
Authenticate a user to a service and optionally extract Kerberos authentication data. When run, the command must be run as a user that has access to the service
principal’s corresponding keytab file.
As I have not used this command so much that I could provide usage examples, better turn to some other cheat-sheet for examples or run man vastool and scroll/search to “vastool auth”. It has pretty good explanation what it does along with the examples.
vastool isvas
Check to see if a given user is an Active Directory user.
Few examples:
-p prints out same info as you get with getent passwd.
vastool kinit
Obtains and caches tickets
You can either authenticate with password:
Or authenticate with keytab:
To verify that you got a ticket, use vastool klist shown below.
vastool klist
List Kerberos tickets stored in a user’s credentials cache.
If you managed to authenticate yourself successfully and get a ticket with vastool kinit then you can list your tickets cache as follows:
vastool kdestroy
Delete tickets from a user’s credential cache.
It drops your ticket cache file along with the tickets inside it. Example would be useless.
vastool license
View currently installed licenses or add new ones.
Feel free to run it to see license info. Also reports how many Unix-enabled users are in use.
If you found this useful, say thanks, click on some banners or donate, I can always use some beer money.
If you like to learn vi/vim macros, how to use tabs, 30+ copy-paste buffers instead of just one – look at my vi&vim cheat-sheet
